We are proud to announce Threatray Release v2.1. Dive in below to discover its highlights.
Integration of Nextron YARA Rules
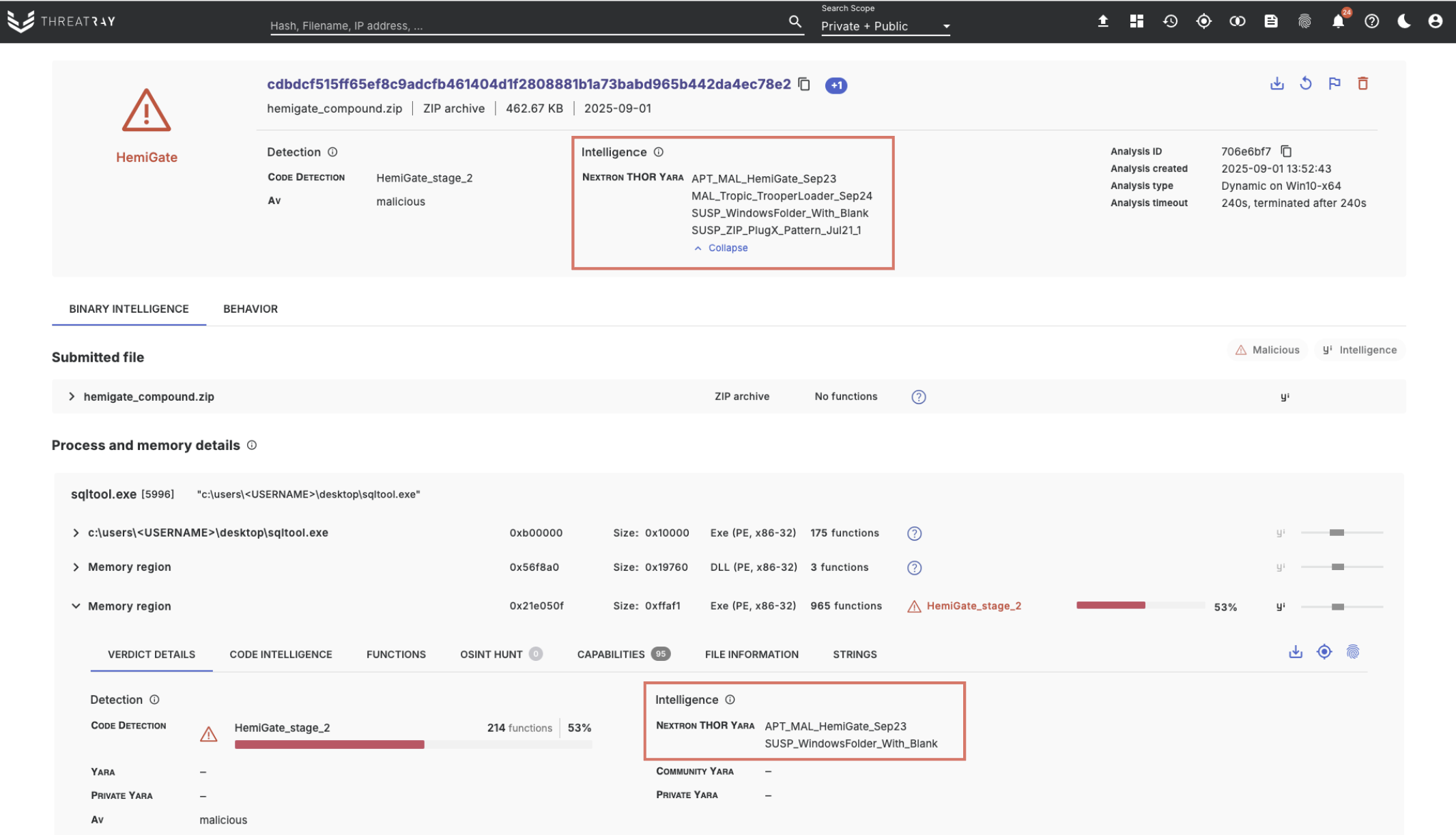
We’ve partnered with Nextron Systems, a pioneer in YARA and Sigma rule detection, to bring their industry-leading detection capabilities directly into Threatray.
What this means for you:
- THOR Thunderstorm YARA detection and classification is now fully integrated into the Threatray platform.
- Every analysis — including all memory dumps — is automatically scanned against Nextron’s YARA ruleset.
- Results are visible in both the overview and memory region sections of your analyses.
By combining Threatray’s cutting-edge code reuse analysis with Nextron’s high-quality YARA rules, we’re taking malware classification to an entirely new level.
Effortless Hunting and Pivoting
Hunting should feel natural — and with our latest release, it is.
- Unified YARA search: Search across all analyses and our malware corpus for YARA rule matches by rule name. Community and Nextron rules are fully indexed and instantly searchable.
- Family name autocomplete: Searching for malware by family is now effortless. Instead of guessing names, autocomplete suggests the families known to Threatray — making it easy to discover and query them directly.
These upgrades make it simpler than ever to pivot through millions of analyses and connect the dots between signatures, YARA hits, families, and related samples.
Here’s a quick example of how it works in practice:


.png)


